主機遭受SQL Injection時,因為攻擊方要探查環境資訊,通常會有大量異常請求,這章來看一下用IDS/IPS從網路封包能看到什麼,產生什麼日誌
建立OpenSource的Snort,與DVWA同一台主機,建立Snort的container
https://hub.docker.com/r/linton/docker-snort
docker run -it --rm --net=host linton/docker-snort /bin/bash
snort -vd
確認有收到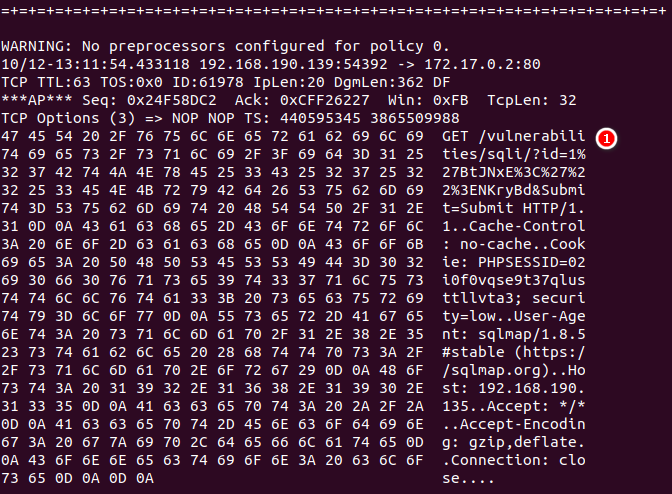
添加規則(這是實驗,一般)
%27 URL_Decode是'
%22 URL_Decode是"
alert tcp any any -> any 80 (msg: "Error Based SQL Injection Detected"; content: "%27" ; sid:100000011; )
alert tcp any any -> any 80 (msg: "Error Based SQL Injection Detected"; content: "%22" ; sid:100000012; )
PS. 實務上為了避免誤判會寫較長的比對
# alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg:"SERVER-WEBAPP Demarc SQL injection attempt"; flow:to_server,established; content:"/dm/demarc"; http_uri; content:"s_key="; content:"'"; distance:0; content:"'"; distance:1; content:"'"; distance:0; metadata:ruleset community, service http; reference:bugtraq,4520; reference:cve,2002-0539; classtype:web-application-activity; sid:2063; rev:13;)
snort -A console -c /etc/snort/etc/snort.conf -l /etc/snort
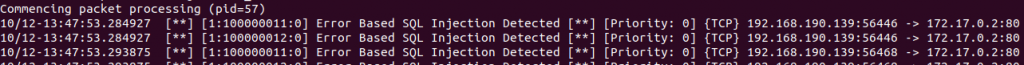
查看完整記錄/etc/snort/snort.log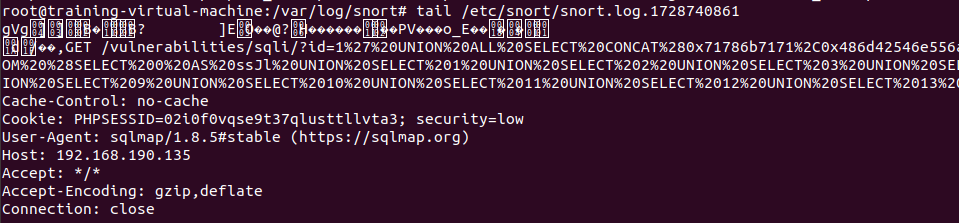
SQLMap 實戰(可怕的 SQL Injection漏洞)
https://atic-tw.blogspot.com/2014/04/sqlmap-sql-injection.html
Detect SQL Injection Attack using Snort IDS
https://www.hackingarticles.in/detect-sql-injection-attack-using-snort-ids/
